Ethereum price breaks through $3,000 after ETH Foundation moves 21,000 ETH in the past two months
Ethereum has surpassed $3,000 in value, following the ETH Foundation transferring a total of 21,000 ETH in the past two months to its internal Gnosis Safe Proxy address.
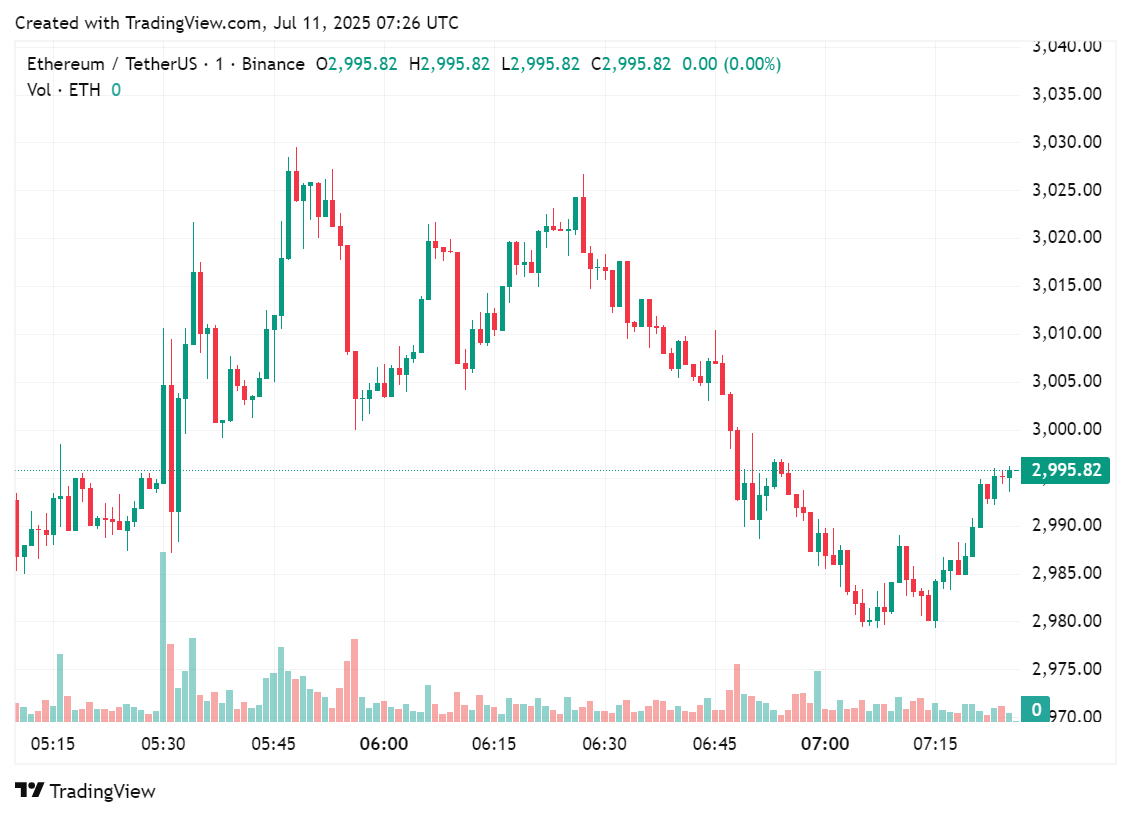
According to data from crypto.news, ETH (ETH) touched on a new high on July 11. The second largest cryptocurrency by market cap has finally surpassed the $3,000 mark. The last time ETH went beyond $3,000 was back in early February before it fell into an extended slump that lasted well into July.
On July 11 at 06:30 AM UTC, ETH bounced back up to a peak price of $3,019. It settled around the $3,000 mark before suffering a slight correction which brough it down to the $2,990 level sometime around 7:00 AM UTC.
At press time, ETH has gone up by 6.6% in the past 24 hours. The token is currently trading hands at $2,987. The token has gone up by 16.8% in the past week and 22% in the past two weeks. It’s daily trading volume has increased by 62.9% compared to the previous trading day. This indicates a rise in recent market activity.
Ethereum Foundation continues to move ETH around
Earlier today, on-chain monitoring firm PeckShield reported that Ethereum Foundation has moved a total of 21,000 ETH or approximately $62.8 million from its main trove to an internal address in the last two months. That address then moved a third of that chunk to a different address, approximately moving 7,000 ETH or $20.9 million.
Afterwards, the third address swapped 1,210 ETH for USDC (USDC) worth $3.5 million within the past 24 hours.
Many traders reacted negatively to the transfer, accusing the ETH Foundation of dumping its own native token. However, there were also traders that came to EF’s defense by stating that it was part of the network’s new treasury policy.
“A lot of FUD going on right now about the Ethereum Foundation selling ETH, don’t believe it!” said a trader with the X handle @digitalartchick.
“The Ethereum Foundation uses it’s 200K ETH treasury to participate in DeFi and generate yield, they do not sell ETH anymore since the leadership change this year,” the user continued in the post.
Earlier in June, the Ethereum Foundation informed the public that it would implement a new treasury strategy that would see the foundation executing more regular ETH sales to maintain a fiat reserve. It would also expand on its staking and DeFi deployments.
You May Also Like

SharpLink Gaming has purchased a total of 232,000 ETH, with a current floating profit of $84.25 million

The Smarter Web Company, a listed company, increased its holdings of 275 bitcoins, bringing its total holdings to 1,275 bitcoins
