Web3 Infrastructure Upgrade: BNB Greenfield Boosts Data Monetization through Decentralized Storage
The “power” of data is self-evident. Many Internet products are free to use because profits can be made from the data provided for free by users. As the digital economy thrives, people have come to recognize data as the backbone and driver of the economy. They also recognized the value of their data and tried to own it, which is the starting point of the Web3 era.
From the birth of Reuther and the emergence of “Reuther killers”, from cloud storage to decentralized storage, data infrastructure continues to expand and improve. BNB Smart Chain (also known as BSC) with the highest active user volume recently launched decentralized storage infrastructure BNB Greenfield, aiming to achieve data-centered synergy of smart contracts, and boost monetization of data in the information era.
Combination of storage with computing
Against the backdrop of exponential growth of data and breach of data privacy, people have been exploring the solution of decentralized storage for nearly a decade. Back in 2014, Storj has been exploring storage services based on blockchain technologies; in 2015, Ria has begun to create distributed cloud system; in the same year, IPFS proposed its decentralized storage solution; in 2017, inspired by IC0 and the token economy model, Freebased File coin and permanent storage solution Ar weave were launched, followed by other public chain-based storage projects.
In fact, public chains like Ethereum also have storage functions. For example, some users recorded their censored publications on Ethereum; Pa News recorded the information of award winners on its annual events. This information will be stored on Ethereum permanently. However, due to limited blockchain capacity and loading speed, public chains like Ethereum are not ideal for massive storage, thus the need for specialized public chains for storage arises.However, distributed storage capacity is not native on Ethereum or EVM public chains, such as Polygon. The only way to make up is to build a storage chain on the public chain.
Another issue emerged. Storage public chain and smart contract public chains are like two separated continents, in particular, most storage public chains are only for data storage and not able to compute and analyze data independently. To build complicated dApps, virtual machines are required to realize smart contract functions. How shoulde we combine decentralized storage and smart contract to provide real-time analysis, implementation and trading, so as to maximize the value of data? This has become a main difficulty and focus in technology development.
As a traditional leader in decentralized storage, Filecoin has been promoting the development of FVM (File coin Virtual Machine) to combine verifiable storage and smart contract function, but the progress has been very slow. According to official data and planning, FVM testnet is expected to be launched in February 2023, and mainnet in May. In view of the fact that Filecoin has a record of delays, whether it will keep its promise this year is still uncertain.
Arweave realized permanent storage of flies through an innovative consensus mechanism. It proposed the concept of “Smart weave” and built some ecosystem projects around it. But the characteristics of Arweave restricted its potential use cases to mainly decentralized H5-APPs, such as media, NFT and web front-ends. Also, Arweave isn’t compatible with Ethereum and it’s hard to do so under the current technological framework. Other storage projects such as Storj and Ria Coin are similar. They are in nature a connection between storage resources without an effective content addressing method, which makes it difficult to share files like movies and audios, showing less competitiveness in storage functionality.
It’s worth mentioning that the early-stage public chain Infinity has realized the smart contract function via the “container” concept, with built-in distributed storage structure. But the ecosystem is less competitive and less integrated among other public chains for its slow progress and EVM incompatibility.
The launch of BNB Greenfield has provided a great solution to the gap between the two major infrastructures. According to BNB Greenfield White Paper, BNB Greenfield dApps are new types of decentralized applications. There are data endpoints, transaction interfaces, P2P networks, and corresponding SDK to help developers to build BNB Greenfield dApps. The use cases officially raised include: personal cloud drive, decentralized front-end web, block chain storage, social media, personal data market and personal digital publishing. If we see data as the petroleum of the digital era, then BNB Greenfield is the Saudi Aramco, providing a series of upstream services including exploration, production, refining and transportation, and downstream companies can further utilize its product for sales or reproduction.
Strengthen the foundation of Web3 with data programmability
Web3 natives accustomed to DeFi mining and NFT minting probably no longer pay attention to the implementation part after clicking “approve”, which are automatically executed by smart contracts. Early in 1994, the renowned cryptologist Nick Sabot, inspired by AVM machines, proposed the concept of “smart contract”. To some extent, AVM can be regarded as the first wave of massive adoption of smart contracts.
If Bitcoin aiming at decentralized peer-to-peer transactions represents the 1.0 era of blockchains, Ethereum with the Turing-complete smart contract functionality is ushering the block chains into the 2.0 era. Only with the smart contract can the blockchain technology be applied to various industries including finance, healthcare, Internet of Things and AI and the smart contract has become one of the cornerstones of the future digital society. Subsequent emerging public chains such as BNB Chain were created to further improve the performance and enhance the computing capabilities of the smart contract on the basis of Ethereum.
However, to bring real changes to the world in the future, the smart contract requires different data support, connection to different systems such as the Internet of Things, Internet and financial system as well as data support from such systems. Unlike the public chain smart contract, the development of which has enabled us to experience many decentralized applications, decentralized data storage is the first step toward development, and the volume of data stored through decentralized storage is much larger than that of traditional storage. And, mass data generated each day will accelerate its production scale only, which makes storage an important and profitable business. According to the IDC report titled Quarterly Tracking Report on Global Corporate Infrastructure: Buyers and Cloud Deployment, it is predicted that the size of the global cloud storage market will reach over USD100 billion between 2020 and 2025.
The reason that centralized storage is important is because it addresses various pain points of the above Web2.0 centralized storage and better caters to the development needs of the big data era. In comparison with traditional centralized storage, the advantages of the decentralized storage mainly lie in protection of privacy, support for edge storage as well as lower costs from co-creation and sharing. According to the IDC report, in the future, 75% of the newly added data will be non-structured edge data. Decentralized data storage has obvious cost advantages for non-structured data in particular. As distributed storage changes the production relationship in the form of nodes and token incentives, it is difficult for the end users to use the services such as storage and indexing at very low prices.
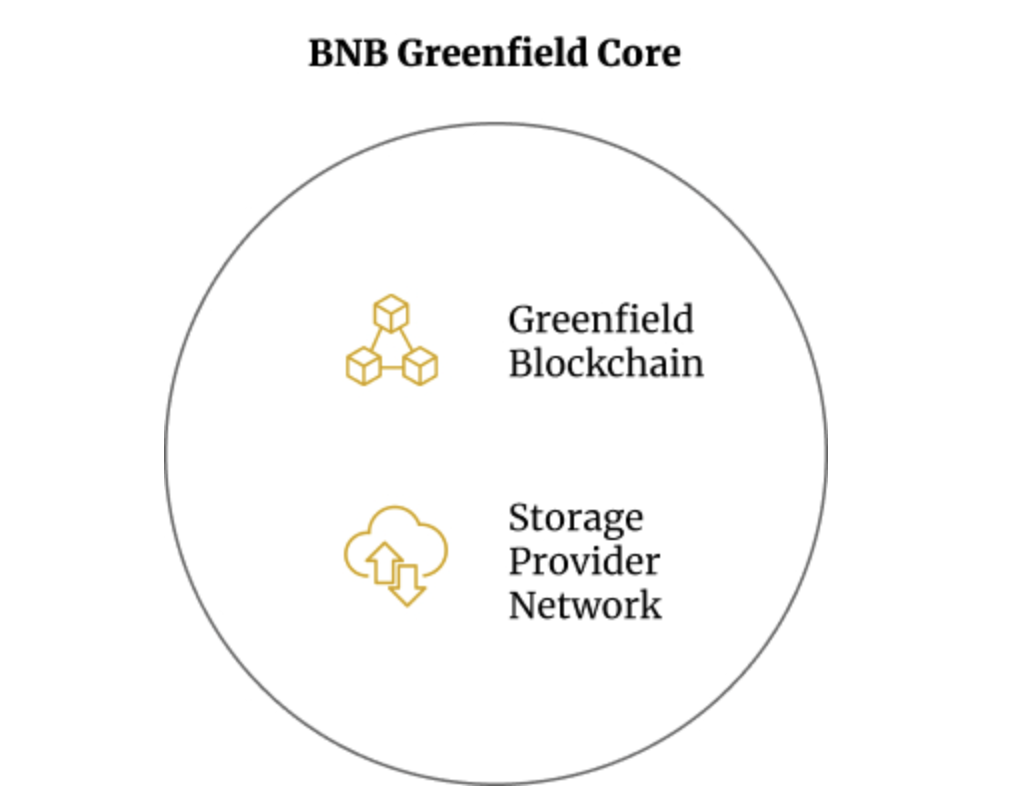
The core infrastructure of BNB Greenfield includes the Greenfield blockchain and SPN (storage provider network). At the beginning, some validators run by the BNB community or SP (storage provider) will initiate BNB Greenfield through genesis , and some SPs will initiate corresponding storage infrastructure and register themselves to the Greenfield blockchain. SPs forms another P2P network, providing the applications and users with a complete function set to create, store, read and exchange data while using the Greenfield blockchain as the metadata and ledger layer.
The real strong point of the Greenfield ecosystem lies in the fact that the platform not only stores data, but also supports value creation based on the data assets and the derived economy. The data asset is characterized firstly in authority, for instance, the authority to read and write data. When such a right is disconnected from the data themselves, they become tradable assets, amplifying the value of the data. When the data themselves can be executed (a new type of “smart contract”), interact with each other and generate new data, this can be amplified. This creates a great space for building a new, data intensive and trustless computing environment.
The BNB Greenfield dApps are also part of the BNB Chain infrastructure and both of them have a native cross-chain bridge. Although it is possible to create and read data on Greenfield Core Infra at lower costs, relevant data operations can be transferred to BSC and integrated with the smart contract systems(for instance, DeFi) there to cause the multiplier effect, which will open up new business opportunities based on data and their operations.
The address format of the Greenfield blockchain will be fully compatible with BSC( and Ethereum). It also accepts EIP-712 transaction signature and verification. This enables the existing wallet infrastructure to interact with Greenfield naturally at the very beginning. Hence, Greenfield will integrate with existing systems and reuse existing infrastructure and dApps, for instance, NFT trading platform, data index and blockchain browser.
The infrastructure core of BNB Greenfield, the Dapp ecosystem of Greenfield and BSC form a “three into one” ecosystem.
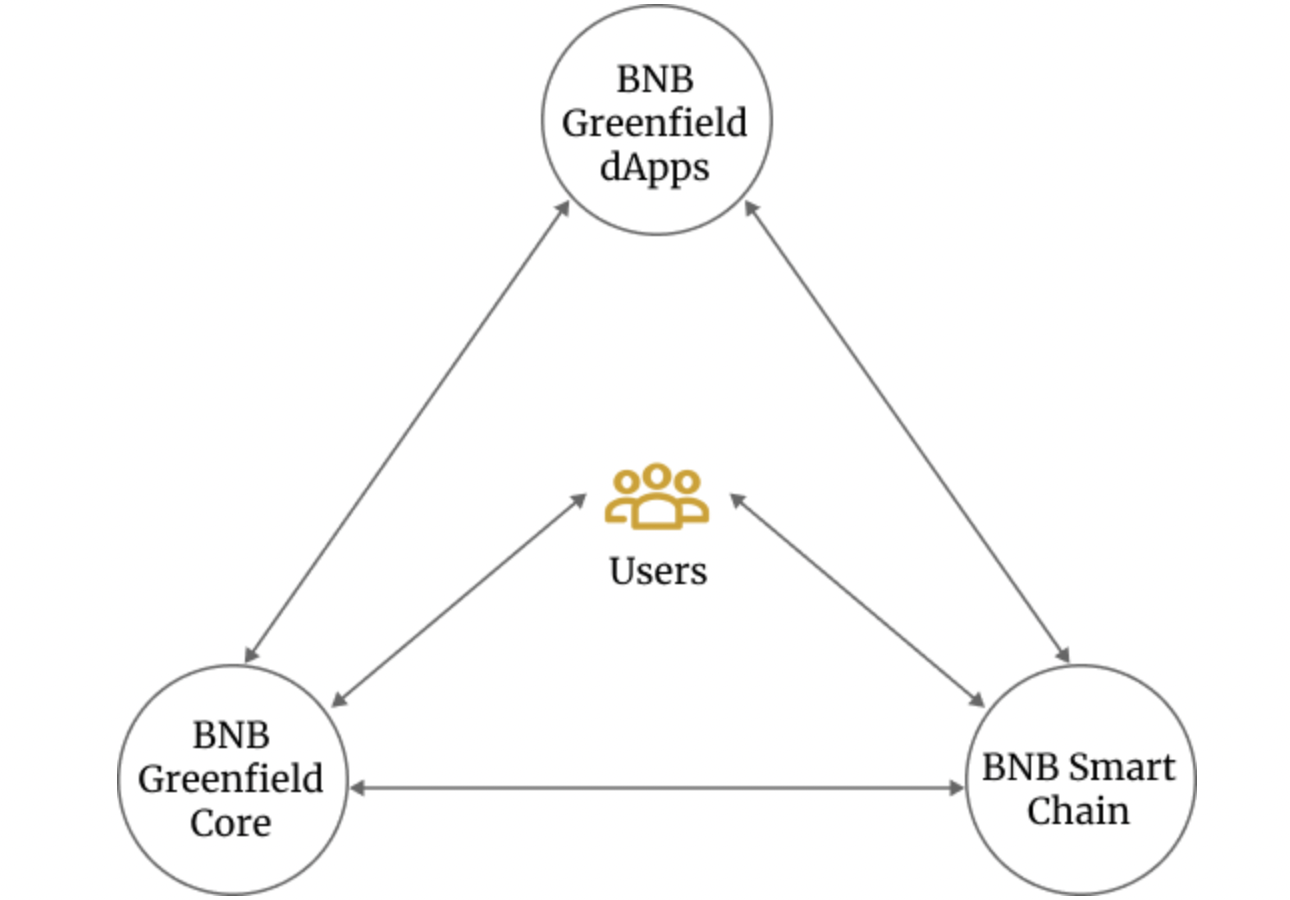
From the perspective of BNB Greenfield DApps, these applications can help the users create, read and execute data on BNB Greenfield, Greenfield SP and BSC and serve the needs of the users. From the perspective of BNB Greenfield, they accept requests and observations from Greenfield dApp on behalf of the users and in the meanwhile accept commands from BSC and work together depending on different business scenarios. From the perspective of BSC, they can accept data assets transferred from BNB Greenfield and provide the new Greenfield dApp with more business scenarios through the smart contract.
In this “three into one” ecosystem, the users can interact with part of the ecosystem directly or indirectly for different purposes.DApps can define how they wish to package the assets from Greenfield to realize the programmability of the data in a real sense.
BNB Integrating a New Function of Decentralized Storage
From the launch of the platform token of Binance until the launch of BNB Smart Chain in September 2022, BNB has evolved from a platform token into an ecosystem token. Today, with the introduction of new use cases, BNB has become the native governance and Gas token of the public chain/BSC sidechain of distributed storage.
There is a native cross-chain bridge between the Greenfield blockchain and BSC. Initially, BNBs are locked on BSC and re-minted on Greenfield. The total supply of BNBs remains unchanged, but they flow among BNB Beacon Chain, BSC and Greenfield. The collection of initial validators of Greenfield upon genesis will lock a certain number of BNBs to the “Greenfield Token Hub” contract on BSC. The contract will also be used as part of the native bridge for transfer following BNB genesis. These BNBs locked initially will be used as the staking and initial Gas fee of the validators.
So far, Greenfield has not disclosed its economy model, for instance, how many BNBs need to be held and staked for the election of the registration and validation nodes of SP and incentive design is needed to ensure there are a suitable number of SPs. SPs need to comply with a series of actions to ensure user’s data redundancy; otherwise, they will be fined.
However, with the launch of Greenfield, some new needs for BNBs arise, for instance, SPs may have the need to purchase or borrow BNBs for staking, and the users need BNBs for paying storage or execution fees in using Greenfield. In the future, if the real-time burn mechanism like that of BSC is implemented, the burning of Gas fee charged by the validation nodes within each block in accordance with the fixed proportion will further reduce the total supply of BNBs in circulation and aggravate the scarcity of BNBs.
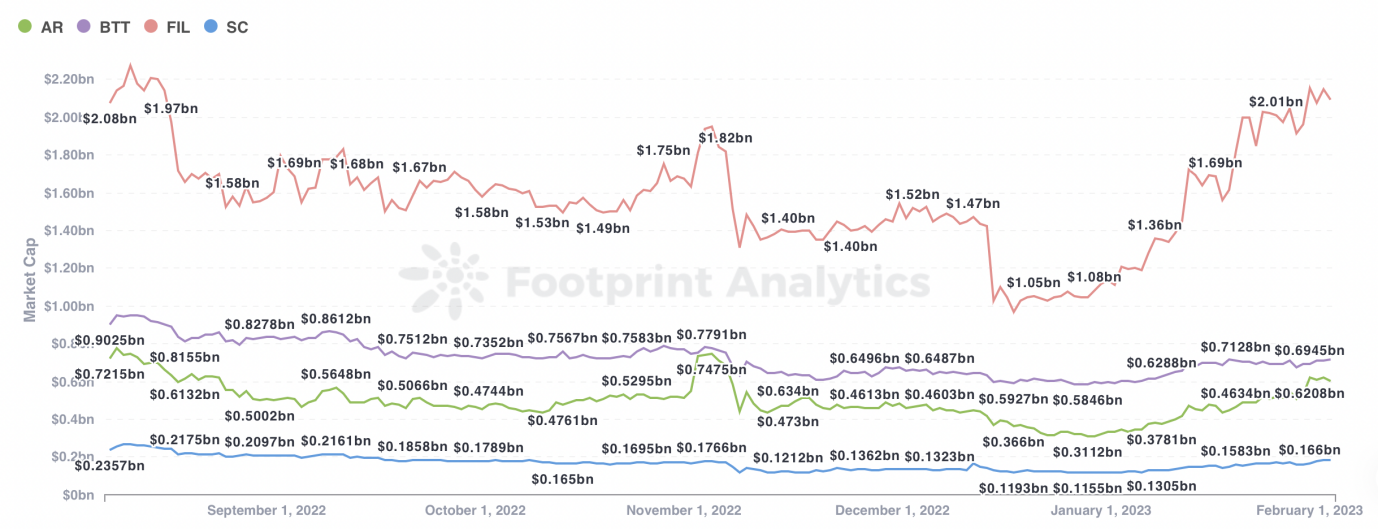
How much value will be added to BNB with the introduction of Greenfield? We can take a look at the existing mainstream decentralized storage projects: FIL boasts the highest market cap of USD 2 billion and Arweave has a total market cap of nearly USD 800 million, both of which are dwarfed before BNB with a total market cap of USD 65 billion. This is because decentralized storage is in the nascent stage of development and there are fewer applications.
However, with the robust need for decentralized storage in the foreseeable future and the development of data programmability, data as the petroleum resource in the new era will be further mined and explored and cause considerable multiplier effects in other areas.
You May Also Like

BDACS Launches KRW1, South Korean Won-Backed Stablecoin, Marking Key Digital Asset Milestone

Bitcoin White Paper: A Peer-to-Peer Cash System
